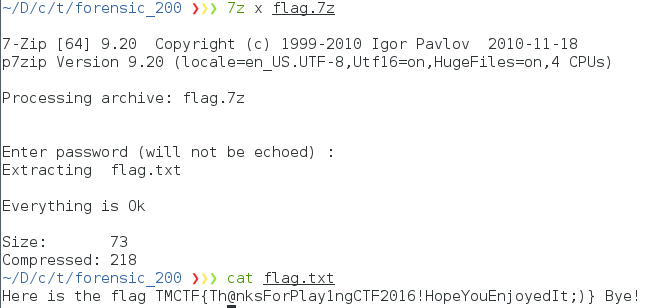
Trend Micro CTF 2016 forensic 200 (en)
The given data is VM image of VMWare.
We started up the image and found “flag” file on Desktop. The task is to find password of flag file.
Why they give live VM ? Is it impossible to solve this task without Windows environment ? (ex. KeyLogger)
We analyzed MFT, evtx, tasks, and found following fact.
\Users\M\Hello.rarexists- flag.7z and Hello.rar is transfered using vmware’s function (drag’n’drop)
- there is no reason using keylogger because flag.7z has been encrypted at first
- suspcious description in
\Windows\System32\Tasks\Microsoft\Windows\Sharing\UpdateLibarycmd /c "vssadmin > %userprofile%\m"- according to
UsnJrnl,\Users\M\mis created in a moment
We got lost and ruined about a day.
Dumping Hello.rar with xxd after a while,
00000e0: ddd2 88d5 481d 3303 0000 0000 0053 544d ....H.3......STM
00000f0: 3a00 5a00 6f00 6e00 6500 2e00 4900 6400 :.Z.o.n.e...I.d.
0000100: 6500 6e00 7400 6900 6600 6500 7200 0c15 e.n.t.i.f.e.r...
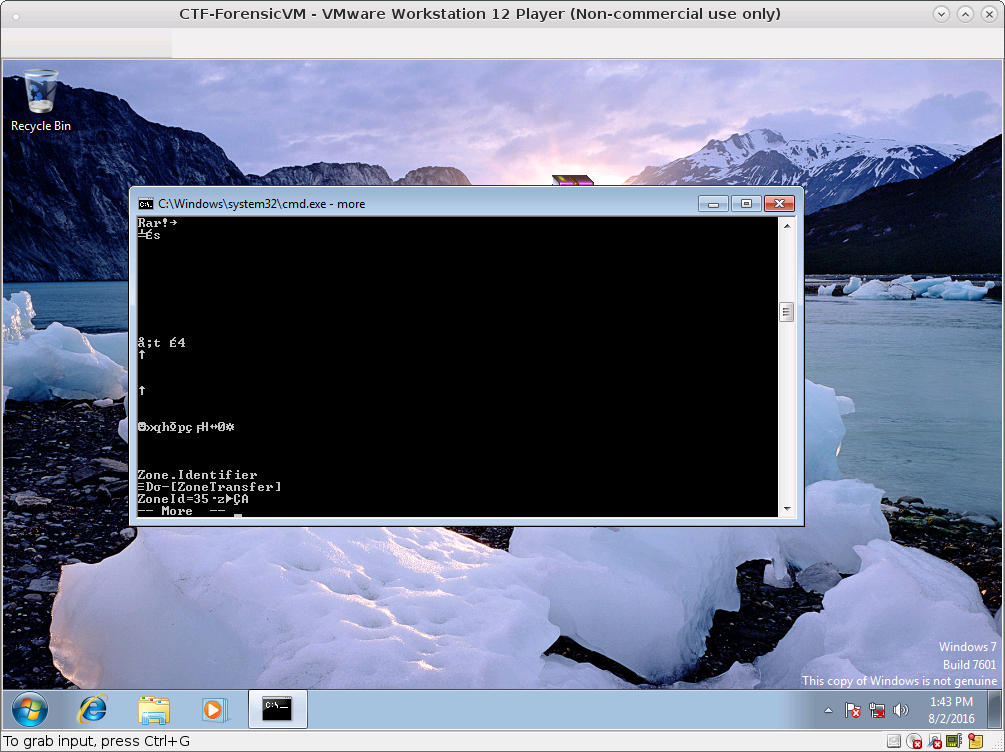
0000110: 0fc5 0d15 5501 1111 e9a7 b289 ec7a 7ba6 ....U........z{.Zone.Identifer!!! We doubt that there is ADS (Alternate Data Stream).
extracting Hello.rar, We found Hello.txt:Zone.Identifer:$DATA.
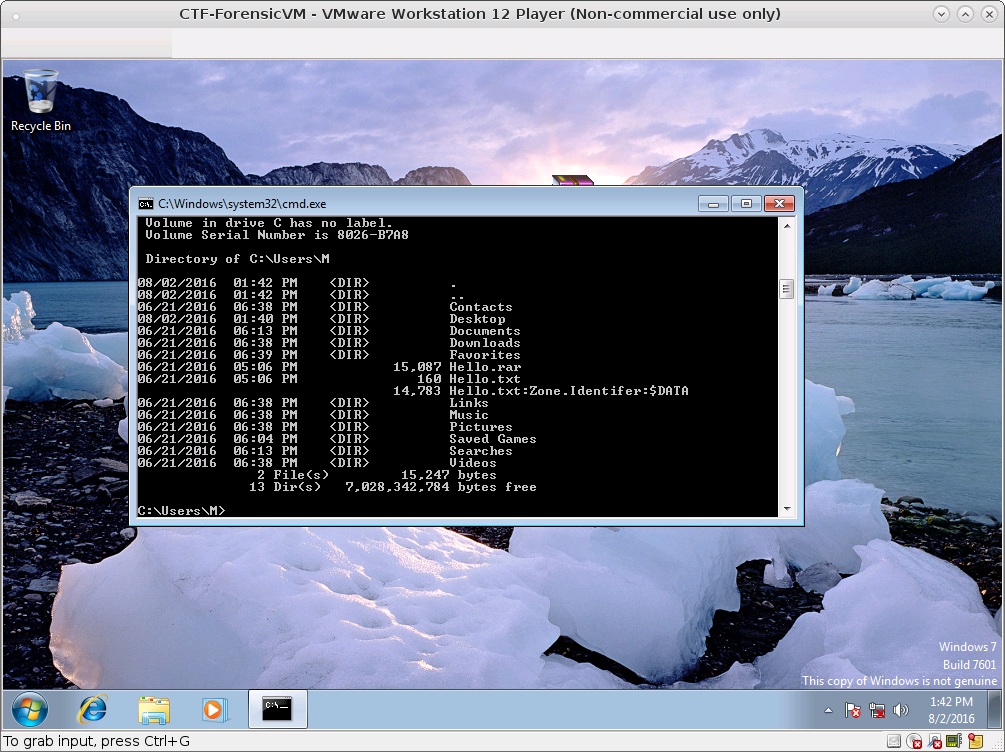
This data seems to be a Rar file.
ADS have to be extracted in NTFS, We used ADSManager.
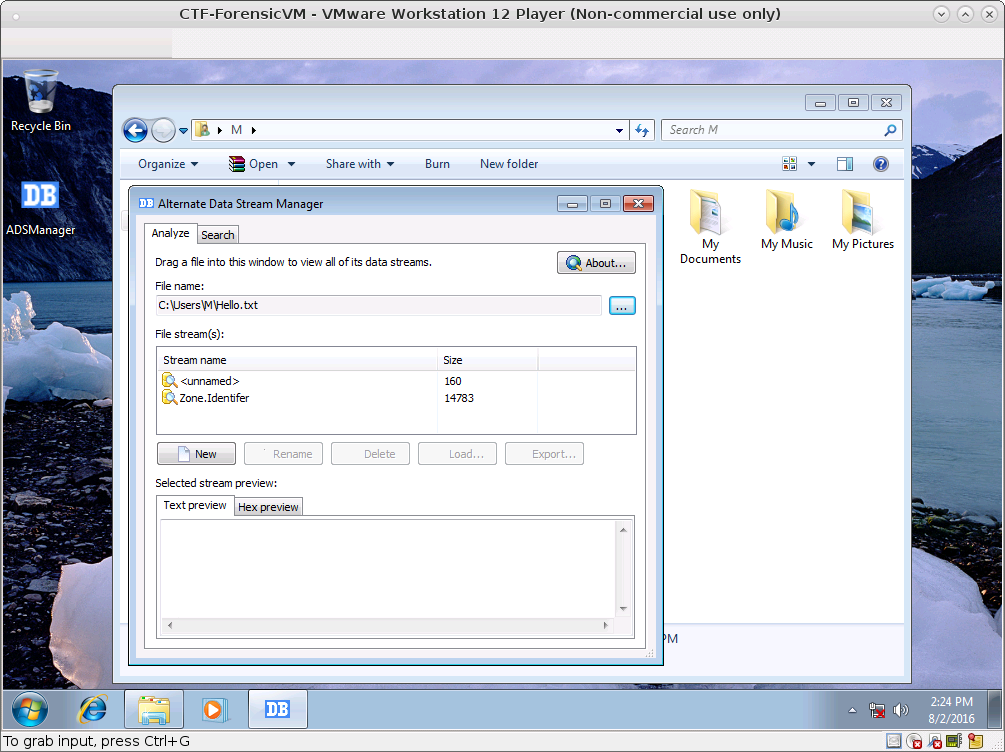
There is more ADS
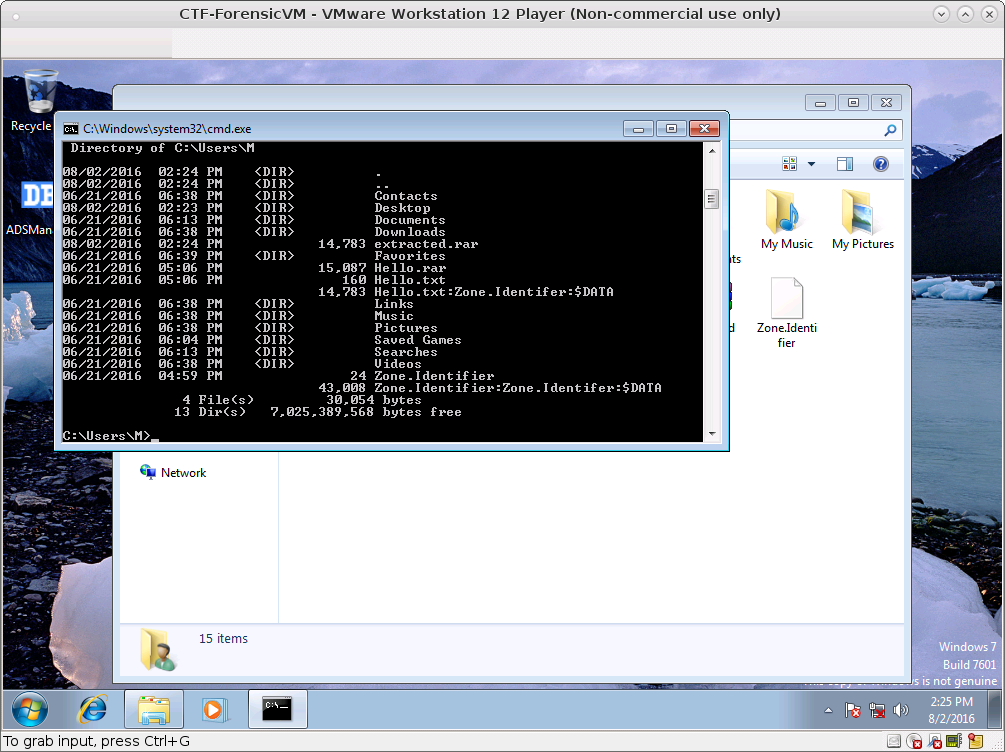
We got Word flie from Zone.Identifer:Zone.Identifer:$DATA
extracted2: Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 950, Template: Normal.dotm, Revision Number: 60, Name of Creating Application: Microsoft Office Word, Total Editing Time: 19:05:00, Create Time/Date: Mon Jun 20 08:42:00 2016, Last Saved Time/Date: Tue Jun 21 03:47:00 2016, Number of Pages: 1, Number of Words: 13, Number of Characters: 75, Security: 0Opening this file with MS Word, and found VBA macro! But the macro cannnot be edited because it is encrypted with password.
We used olevba to extract macro.
FILE: extracted2
Type: OLE
-------------------------------------------------------------------------------
VBA MACRO ThisDocument.cls
in file: extracted2 - OLE stream: u'Macros/VBA/ThisDocument'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Private Sub Document_Close()
CTFpo.CTF
End Sub
-------------------------------------------------------------------------------
VBA MACRO CTFpo.bas
in file: extracted2 - OLE stream: u'Macros/VBA/CTFpo'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Sub CTF()
'Created by MC.
On Error GoTo Handler
'a FileSystemObject.
Set fso = CreateObject("Scripting.FileSystemObject")
Dim fname, passOne, passTwo, sTemp, sFlagEnc As String
Dim fLength As Integer
' Create a TextStream.
Set stream = fso.OpenTextFile("install.log", 1)
sTemp = stream.Readline
fLength = Int(Mid(sTemp, 2, 1))
fname = Left(sTemp, 1 + fLength)
passOne = Mid(sTemp, 2)
stream.Close
Set streamTwo = fso.OpenTextFile(fname, 1)
sTemp = streamTwo.Readline
passTwo = Left(sTemp, 8)
streamTwo.Close
passOne = Replace(passOne + passTwo, " ", "")
If Day(Now()) > 30 And Minute(Now()) > 58 Then
MsgBox passOne, vbInformation, "It is what you are looking all along.."
End If
Handler:
End Sub
Private Function Decrypt(key As String, encrypted As String)
On Error Resume Next:
Do While (Len(key) < Len(encrypted))
key = key + key
Loop
For i = 1 To Len(encrypted):
Decrypt = Decrypt & Chr(Asc(Mid(key, i, 1)) Xor Asc(Mid(encrypted, i, 1)))
Next:
End FunctionWe rewrote CTF() function with python.
# decode.py
stream = open('install.log')
stemp = stream.readline().strip()
flength = int(stemp[1:2])
fname = stemp[:1+flength]
passone = stemp[1:]
stream.close()
stream2 = open(fname)
stemp = stream2.readline().strip()
passtwo = stemp[:8]
stream2.close()
passone = (passone+passtwo).replace(' ', '')
print passoneWe took install.log from VM (\Users\M\install.log) and executing this script, It says “No such file or directory ‘M’”. So we recovered ‘M’ using description of Tasks.
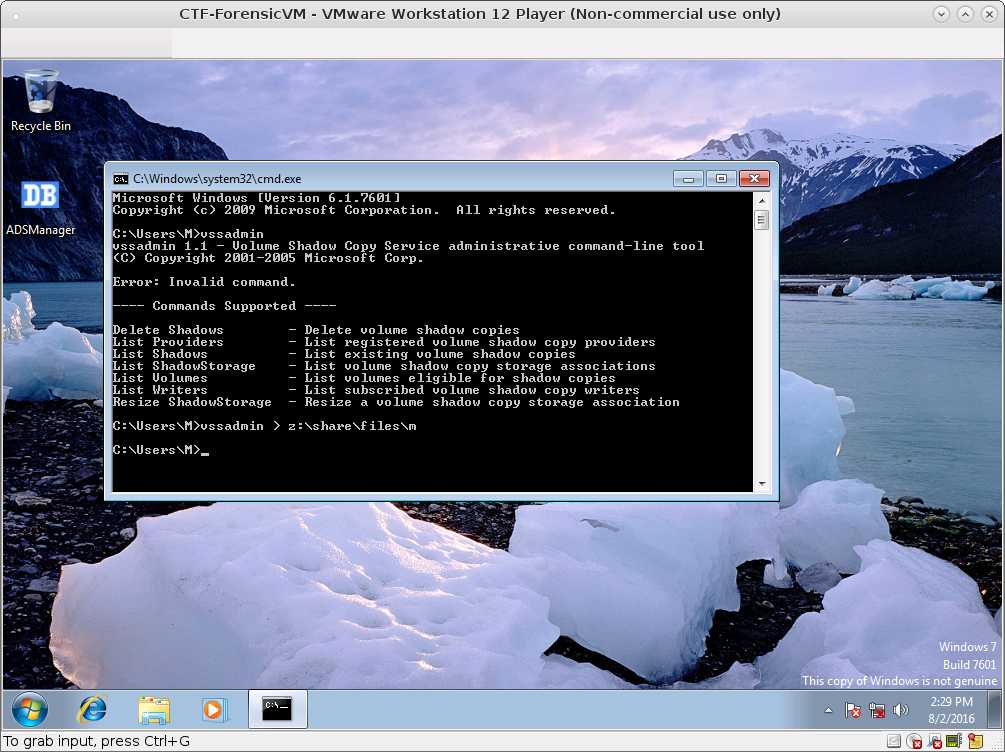
Executing the script, we got 0zillaFirefoxInstallationStarted:2015-09-0715:18:16vssadmin.
Decrypted flag.7z using the password, and got flag.